
Unknown threat actors are actively targeting two critical zero-day vulnerabilities that allow them to bypass two-factor authentication and execute malicious code inside networks that use a widely used virtual private network appliance sold by Ivanti, researchers said Wednesday.
Ivanti reported bare-bones details concerning the zero-days in posts published on Wednesday that urged customers to follow mitigation guidance immediately. Tracked as CVE-2023-846805 and CVE-2024-21887, they reside in Ivanti Connect Secure, a VPN appliance often abbreviated as ICS. Formerly known as Pulse Secure, the widely used VPN has harbored previous zero-days in recent years that came under widespread exploitation, in some cases to devastating effect.
Exploiters: Start your engines
“When combined, these two vulnerabilities make it trivial for attackers to run commands on the system,” researchers from security firm Volexity wrote in a post summarizing their investigative findings of an attack that hit a customer last month. “In this particular incident, the attacker leveraged these exploits to steal configuration data, modify existing files, download remote files, and reverse tunnel from the ICS VPN appliance.” Researchers Matthew Meltzer, Robert Jan Mora, Sean Koessel, Steven Adair, and Thomas Lancaster went on to write:
Volexity observed the attacker modifying legitimate ICS components and making changes to the system to evade the ICS Integrity Checker Tool. Notably, Volexity observed the attacker backdooring a legitimate CGI file (compcheck.cgi) on the ICS VPN appliance to allow command execution. Further, the attacker also modified a JavaScript file used by the Web SSL VPN component of the device in order to keylog and exfiltrate credentials for users logging into it. The information and credentials collected by the attacker allowed them to pivot to a handful of systems internally, and ultimately gain unfettered access to systems on the network.
The researchers attributed the hacks to a threat actor tracked under the alias UTA0178, which they suspect is a Chinese nation-state-level threat actor.
Like other VPNs, the ICS sits at the edge of a protected network and acts as the gatekeeper that’s supposed to allow only authorized devices to connect remotely. That position and its always-on status make the appliance ideal for targeting when code-execution vulnerabilities in them are identified. So far, the zero-days appear to have been exploited in low numbers and only in highly targeted attacks, Volexity CEO Steven Adair said in an email. He went on to write:
However, there is a very good chance that could change. There will now be a potential race to compromise devices before mitigations are applied. It is also possible that the threat actor could share the exploit or that additional attackers will otherwise figure out the exploit. If you know the details—the exploit is quite trivial to pull off and it requires absolutely no authentication and can be done over the Internet. The entire purposes of these devices are to provide VPN access, so by nature they sit on the Internet and are accessible.
The threat landscape of 2023 was dominated by the active mass exploitation of a handful of high-impact vulnerabilities tracked under the names Citrix Bleed or designations including CVE-2023-36934, CVE-2022-47966, and CVE-2023-49103, which resided in the Citrix NetScaler Application Delivery Controller and NetScaler Gateway, MOVEit from maker Progress Software, 24 wares sold by Zoho-owned ManageEngine and ownCloud, respectively. Unless affected organizations move more quickly than they did last year to patch their networks, the latest vulnerabilities in the Ivanti appliances may receive the same treatment.
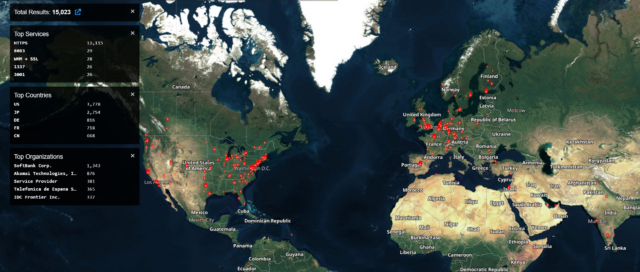
Researcher Kevin Beaumont, who proposed “Connect Around” as a moniker for tracking the zero-days, posted results from a scan that showed there were roughly 15,000 affected Ivanti appliances around the world exposed to the Internet. Beaumont said that hackers backed by a nation-state appeared to be behind the attacks on the Ivanti-sold device.
Shodan











![ROSE IN DA HOUSE I BE MY BOYFRIENDS 2 [OFFICIAL TRAILER]](https://cherumbu.com/wp-content/uploads/2022/01/ROSE-IN-DA-HOUSE-I-BE-MY-BOYFRIENDS-2-OFFICIAL-150x150.jpg)

